|
KAoS Policies
for controlling JAAS- based application |
|
|
|
|
|
|
1. Introduction |
|
|
| |
The Java
Authentication and Authorization Service (JAAS) is a Java package that permits the management of the user
authentication and the control of the access of authenticated
users to system resources.
JAAS is an
extension of the Java Security architecture and has now been integrated in
the Java 2
SDK, v 1.4. In particular, it
adds to the traditional Java security mechanisms the possibility to
manage permissions that are based on the name of the authenticated user,
and not only on the code characteristics such as the code source. JAAS
can be used as a means to control the access of software agents to
resources, by associating agents to one or more principals (representing
the agent themselves or the humans running them) and then using the JAAS
permissions for controlling them.
KAoS
supports the control of Java applications that are controlled by
JAAS by means of the KAoS policies instead of the traditional java
permissions. The integration of the KAoS platform with the application
to control does not require any adaptation of the application code. Using
KAoS for controlling the application can bring
some advantages in the security management of the application:
-
The policy
specification can be simplified through the assistance of KPAT
-
KAoS
policies can extend the limited semantic of the traditional Java
policies (for
example, in KAoS it is possible to specify and reason over both negative and positive
authorization policies, while Java manages only positive authorizations)
-
Users can benefit from the
usage of the set tools provided by KAoS for the policy management. For
example, policy
conflicts can be automatically detected at specification time
|
In this tutorial we briefly present how to use the KAoS components that
permit to bridge a JAAS-based application with KAoS. Because this
solution does not require any adaptation of the code of the application
to control, it can be viewed as a very simple example of policy enforcement
automation, and it has been using as a case study for our research
in this field. |
|
| |
|
2. Architecture Overview |
|
2.1 JAAS |
| |
The JAAS authorization is based on the name
of the authenticated user and on the set of Java permissions that are assigned
to him. Any user is represented in terms of a
subject. A subject can be associated to one or more principals that
represent the different usernames with which an user can be recognized within
the system. Then, the permission to execute is granted to a subject
based on its authenticated principals. For example, the following policy
assigns the permission to read a file to the principal 'gianluca': |
| |
| |
|
|
| |
grant Principal
sample.principal.SamplePrincipal
“gianluca" {
permission java.io.FilePermission "A.txt",
"read";
};
|
|
Example of JAAS Policy: the user "gianluca" is permitted
to read the
file called "A.txt" |
| |
JAAS relies on the Java Security mechanisms to assure a
correct enforcement of its policies. In particular, the Java Security
architecture relies on the following basic components:
-
AccessController:
implements a default access control algorithm to grant or deny
accesses to resources;
-
SecurityManager: the responsible of
policy checking. It can prevent the completion of an operation by
throwing a security exception;
-
Class Loader: provides loaded classes with
separate namespaces and associates classes with protection domains;
-
Policy Provider: retrieves permissions
granted to classes/users.
|
| |
|
|
|
2.2 Integration of KAoS with JAAS |
| |
The Java Security platform
can be extended to support customized policy enforcements. This property
permits to easily interface KAoS with JAAS. In particular, the
substitution (from the outside of the application) of the standard
Security Manager and Policy Provider with customized components provided
by KAoS permits to redirect the checking of the permission from the Java
Security Architecture to the KAoS
framework. Then KAoS can manage the security checking accordingly with its set
of policies as shown in the following picture: |
| |
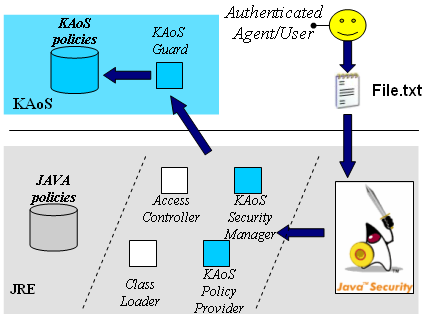
Integration of KAoS with the Java Security Architecture
|
| |
In particular, when an
authenticated agent tries to access a resource controlled by JAAS, the
native Java code automatically intercepts this attempt and triggers a
security checking of the current permissions by calling the Java Security.
This call is redirect by the KAoS customized components to the KAoS
framework where the KAoS policies can be enforced instead of the
traditional Java ones. |
| |
|
|
|
3. A running example |
| |
The
source code of the JAAS-based application we have used as case-study is
stored in the directory:
[KAoS-HOME]\source\Jaas\DemoSunJAAS
This demo is
based on the example code provide by Sun in the
JAAS tutorial. The
application enforces the authentication of users and for each user
successfully authenticated it creates an agent that
tries to read a local file that is called "A.txt"
-
For compiling the code run the script
[KAoS-HOME]\scripts\win\grid\ProxyToJaas\DemoSunJAAS\compile.bat
This
script creates also the jar files used for running the application
in the directory:
[KAoS-HOME]\source\Jaas\DemoSunJAAS
|
|
[KAoS-HOME]\scripts\win\grid\ProxyToJaas\DemoSunJAAS\Go.bat |
In particular, at the
beginning the application authenticates an user by requiring an
username and a password: |
| |
| |
-------------------------------------------------------
This agent tries to read the file "A.txt"
To launch it an authentication is required.
---------------------------------------------------------
user name: {any username}
password: kaos |
|
| |
Application Output: Authentication phase |
|
|
| |
Any username
can be used for the authentication while only 'kaos' can be used as a
permitted password, otherwise the authentication fails. If the
authentication succeeds, an agent (i.e. an instance of the class
sample.MyThread) is created and linked to a principal with the same name
of the username used during the authentication. When the agent tries to
read the file "A.txt" the Java Security retrieves the set of
permissions associated with its principal, by reading the file:
[KAoS-HOME]\scripts\win\grid\ProxyToJaas\DemoSunJAAS\sampleazn.policy
This file
assigns the permission to read the file "A.txt" only to principals called
"gianluca". So if the user has been authenticated with the
username 'gianluca', he can read the content of the file, otherwise the
permission is denied. |
| |
| |
-----------------------------------------------------------------
This agent tries to read the file A.txt
To launch it an authentication is required.
-----------------------------------------------------------------
user name: gianluca
password: kaos
[SampleLoginModule] user entered user
name: gianluca
[SampleLoginModule] user entered
password: kaos
[SampleLoginModule] authentication
succeeded
[SampleLoginModule] added
SamplePrincipal to Subject
Authentication succeeded!
Authenticated user has the following Principals:
SamplePrincipal: gianluca
User has 0 Public Credential(s)
*** Trying to read file ***
--> THIS IS THE CONTENT OF THE FILE A.TXT
*** End of THREAD execution *** |
|
-----------------------------------------------------------------
This agent tries to read the file A.txt
To launch it an authentication is required.
-----------------------------------------------------------------
user name: otherName
password: kaos
[SampleLoginModule] user entered user
name: otherName
[SampleLoginModule] user entered
password: kaos
[SampleLoginModule] authentication
succeeded
[SampleLoginModule] added
SamplePrincipal to Subject
Authentication succeeded!
Authenticated user has the following Principals:
SamplePrincipal: otherName
User has 0 Public Credential(s)
*** Trying to read file ***
Permission to read is denied
*** End of THREAD execution *** |
|
|
Application Output: Authorization phase with permission granted |
|
Application Output: Authorization phase with permission denied |
|
|
| |
|
|
|
4. Controlling the
application with KAoS |
| |
In addition
to the core components for the policy management, KAoS provides some
specific components for controlling the JAAS applications. The source
code and classes of these components can be found in the
following directories:
[KAoS-HOME]\source\Jaas\policyManagement
[KAoS-HOME]\source\Jaas\ontology |
| |
The current solution relies on a proxy agent
(an instance of the class Jaas.policyManagement.KAoSProxyToJaas) that is
running on the CoABS Grid
and that accepts some requests from external Java applications. For the
communication, the proxy agent open a socket at port 55. On the
application-side, any checking of permissions is redirect to this agent
through the socket. On the KAoS-side, KAoS associates a Guard to the
proxy agent that manages the policy reasoning and checking at any
redirected request. |
| |
|
| |
4.1
Configuration of the KAoS policy framework |
| |
Within KAoS,
for running
the proxy agent that permits to bridge the KAoS framework
with the application to control, the following steps are required:
-
Compile the code of the components required for interfacing KAoS with
any JAAS application and build the kJass.jar file by running the following scripts:
[KAoS-HOME]\scripts\win\jaas\compile_kJaas.bat
[KAoS-HOME]\scripts\win\jaas\build_kJaas_jar.bat
The correct execution of this two scripts create the kJaas.jar file
in the directory [KAoS-HOME]\lib; |
-
Run the CoABS Grid;
|
-
Run the following scripts and in the
following order:
[KAoS-HOME]\scripts\win\grid\ProxyToJaas\1_DirectoryService.bat
[KAoS-HOME]\scripts\win\grid\ProxyToJaas\2_TestDomainManager.bat
[KAoS-HOME]\scripts\win\grid\ProxyToJaas\3_startServletRunner.bat
[KAoS-HOME]\scripts\win\grid\ProxyToJaas\4_start_KPAT.bat; |
-
With KPAT, create a domain called "TestDomain"
with a default modality= 'NegAuthorizationPolicy'. This will be
the domain of the agent proxy;
|
-
With
KPAT, load the predefined namespace:
http://ontology.ihmc.us/Java/JavaOntologies.owl that
contains the ontologies for JAAS;
|
-
With
KPAT, load the namespace:
http://www.lia.deis.unibo.it/Staff/GianlucaTonti/DAML/JaasInstances.daml
that contains the description of the file "A.txt" as an instance of
the class 'File'; |
-
Run the agent proxy by executing the
following script:
[KAoS-HOME]\scripts\win\grid\ProxyToJaas\5_KAoSProxyToJaas.bat
This
agent will open a graphical interface (shown in the following
picture) that permits to create instances of Principals to control. |
| |
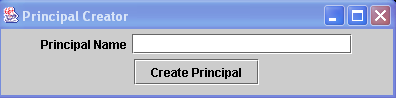 |
|
| |
Graphical Interface for creation
of the Principals to control in KPAT |
|
|
| |
4.2
Configuration of the JAAS application |
|
| |
To control the JAAS application with KAoS, it
is required to substitute the traditional java Policy provider and
Security Manager with customized KAoS components. This can be
easily done from the outside of the application, without changing the
application code, by performing the following steps: |
| |
-
To install the KAoS PolicyProvider, it is required to change the
security configuration file of the current Java virtual machine (usually stored
in [JDK-PATH]\jre\lib\security\java.security), by linking the
policy.provider property to the customized Policy Provider
provided by KAoS. To do this, change the configuration file in the
following way:
OLD LINE TO REM:
policy.provider=sun.security.provider.PolicyProvider
NEW LINE TO ADD:
policy.provider=sun.security.provider.PolicyProvider
|
| |
-
For changing the Security Manager and running the Demo, run
the following script:
[KAoS-HOME]\scripts\win\grid\ProxyToJaas\DemoSunJAAS\GO_KAoS.bat |
| |
After the execution of this two steps the
application requires the user authentication as usual, but this time the
checking of any permissions is performed by KAoS. If no policy has
been defined in KAoS the permission is denied for any principal as shown
in the following ouput: |
| |
| |
Try
connecting to KAoSProxyToJaas 127.0.0.1
Connected to: /127.0.0.1 on port: 55
-----------------------------------------------------------------
This agent tries to read the file A.txt
To launch it an authentication is required.
-----------------------------------------------------------------
*** Using new KAoS policy provider for Java 1.4 ***
user name: gianluca
password: kaos
[SampleLoginModule]
user entered user name: gianluca
[SampleLoginModule]
user entered password: kaos
[SampleLoginModule]
authentication succeeded
[SampleLoginModule]
added SamplePrincipal to Subject
Authentication succeeded!
Authenticated user has the following Principals:
SamplePrincipal: gianluca
User has 0 Public Credential(s)
*** Trying to read file ***
**** Checking policies for the Subject ***
Checking policies for gianluca
Querying the KAoSproxyToJaas agent and the Guard about:
(kaos.policy.guard.ActionPermission
gianluca)
Read: false
**** End of Checking ***
Permission to read is denied
*** End of THREAD execution *** |
|
| |
Application Output:
permission to read denied by KAoS |
|
|
|
|
|
|
4.3
Specification of KAoS policies with KPAT |
| |
Assign the permission to read a file with
KPAT is very simple. As a guiding example, the following steps show how
to create a policy that assigns the authorization to read the file "A.txt"
to a principal called "userTest" : |
| |
-
Create an
instance of the Principal to control by using the graphical interface
provided after the creation of the agent proxy (see
Section 4.1);
| |
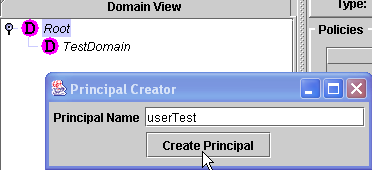 |
|
| |
Creation of the principal 'userTest' |
|
|
|
-
Press the
'Refresh' button to update the graphical interface. If the Principal
has been correctly created the Domain window reports a similar tree:
| |
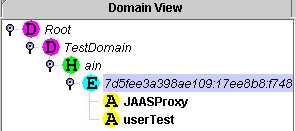 |
|
| |
Example of correct initialization of the
management domain |
|
|
|
-
Select the
'userTest' principal in the Domain tree and add to it a policy by
pressing the button 'Add'. Then authorize the 'userTest' to
perform a 'ReadFileAction' by using the KAoS policy editor in the
following way:
| |
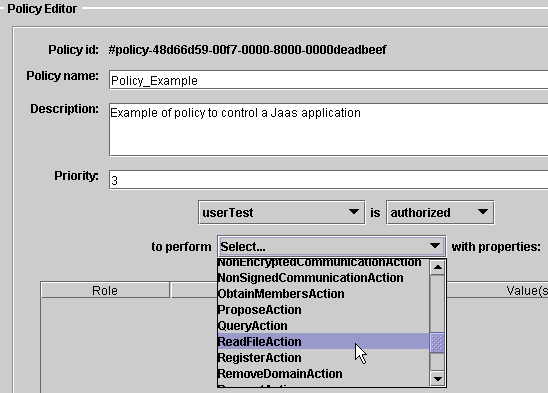 |
|
| |
Policy specification: userTest
can perform a 'ReadFileAction' action |
|
|
| |
-
Specify the permitted file
to read through the property 'AccessedEntity':
| |
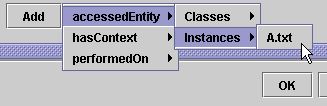 |
|
| |
Policy specification: permission
to access the file A.txt |
|
|
| |
-
At the end
of the policy specification, remember to activate the policy by
pressing the button 'Commit'.
|
| |
At the end of the specification of this
policy, any user authenticated by the JAAS application (see
Section 4.2) with the username 'userTest' is
authorized by KAoS to read the content of the file 'A.txt' |
| |
| |
Try
connecting to KAoSProxyToJaas 127.0.0.1
Connected to: /127.0.0.1 on port: 55
-----------------------------------------------------------------
This agent tries to read the file A.txt
To launch it an authentication is required.
-----------------------------------------------------------------
*** Using new KAoS policy provider for Java 1.4 ***
user name: userTest
password: kaos
[SampleLoginModule] user entered user
name: userTest
[SampleLoginModule] user entered
password: kaos
[SampleLoginModule] authentication
succeeded
[SampleLoginModule] added
SamplePrincipal to Subject
Authentication succeeded!
Authenticated user has the following Principals:
SamplePrincipal: userTest
User has 0 Public Credential(s)
*** Trying to read file BY THREAD3 ***
**** Checking policies for the Subject ***
Checking policies for userTest
Querying the KAoSproxyToJaas agent and the Guard about:
(kaos.policy.guard.ActionPermission
userTest)
Read: true
**** End of Checking ***
--> THIS IS THE CONTENT OF THE FILE A.TXT
*** End of THREAD execution *** |
|
| |
Application
Output: permission to read is authorized
by KAoS
after the policy specification |
|
|
|
|





